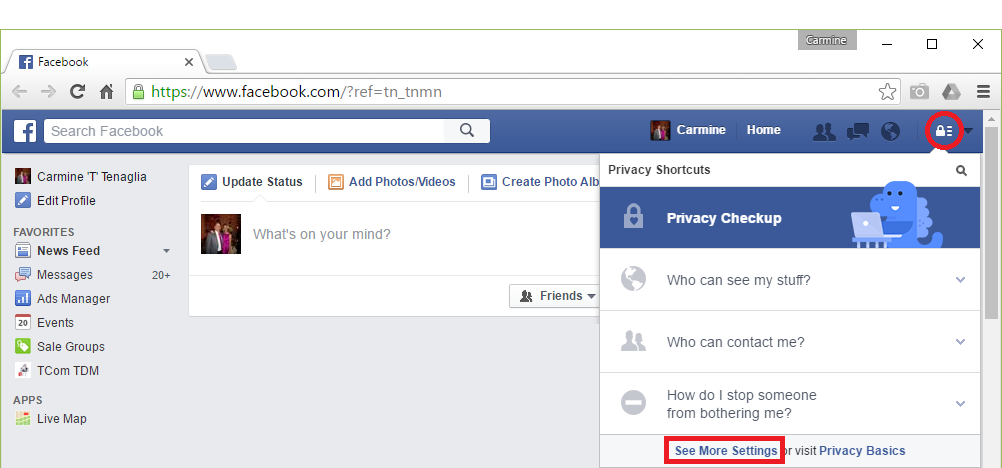
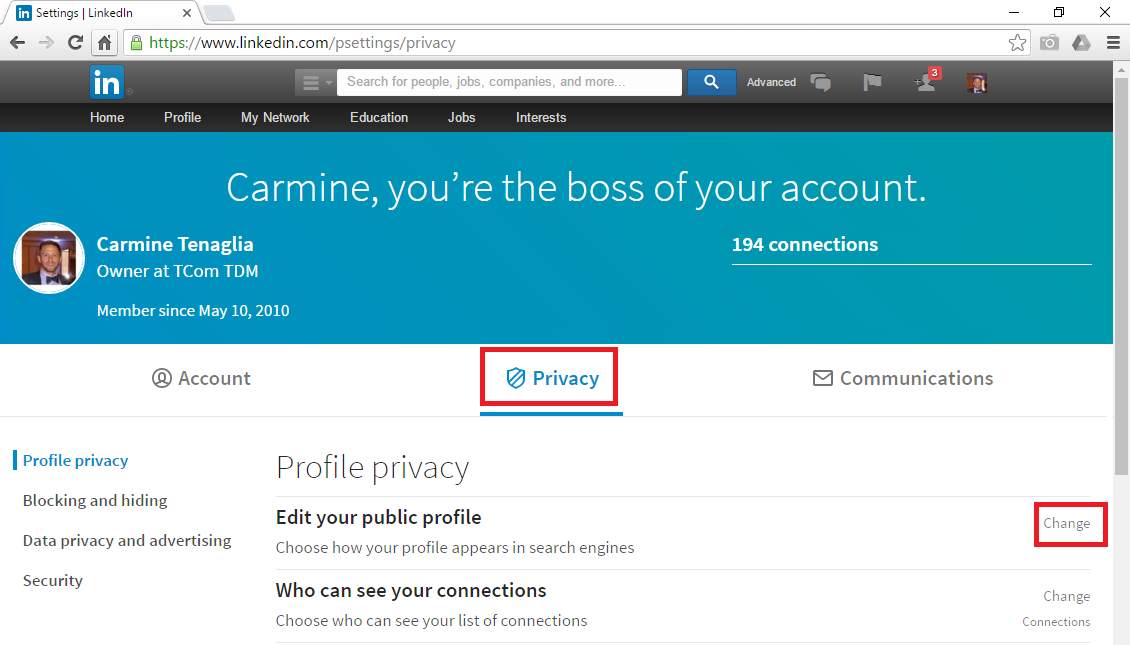
How to setup exchange on Android
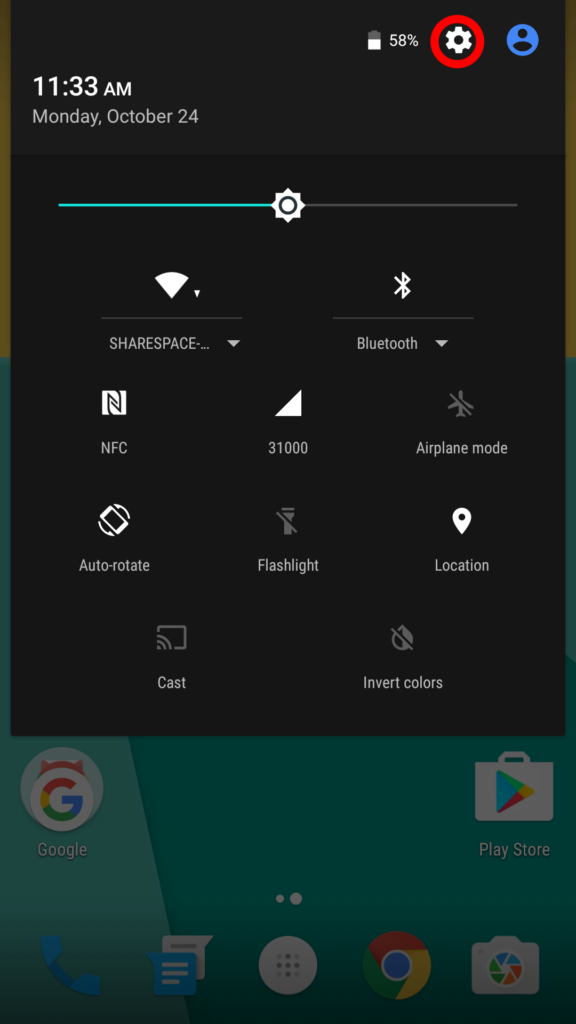
1. Swipe Down from the top of your screen to access the quick settings.
2. Tap the small gear icon in the top right corner.
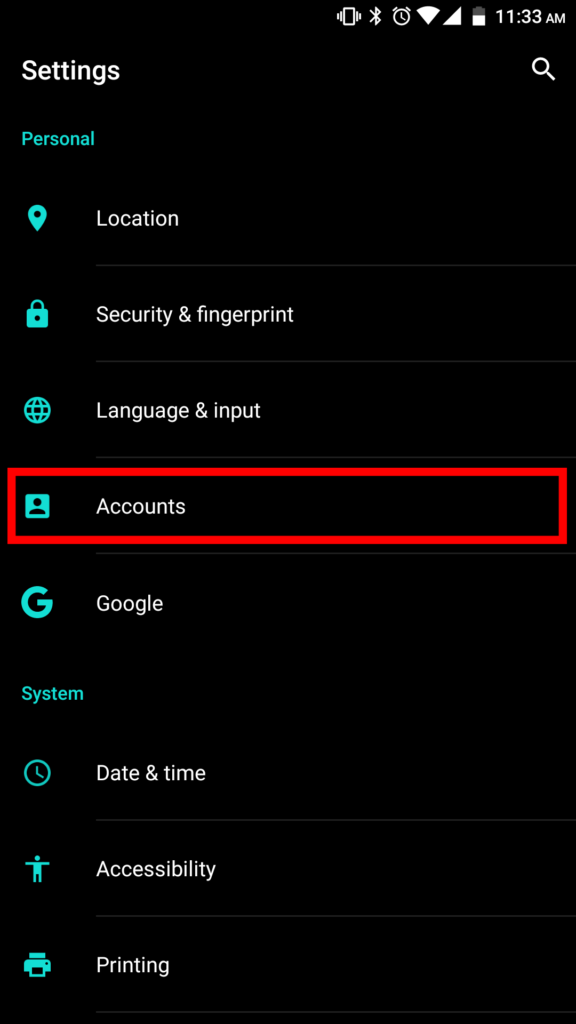
3. Scroll down and select “Accounts”
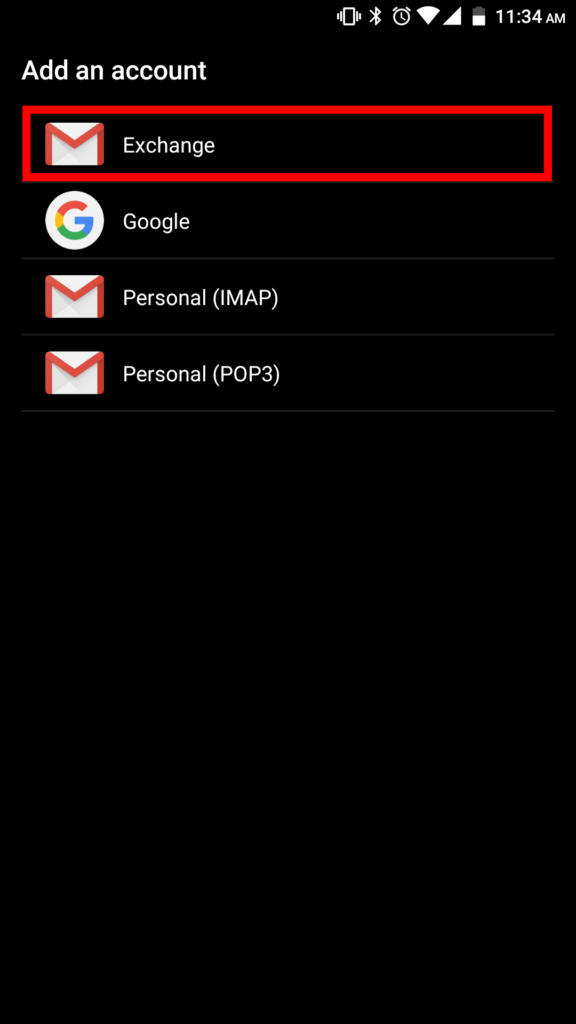
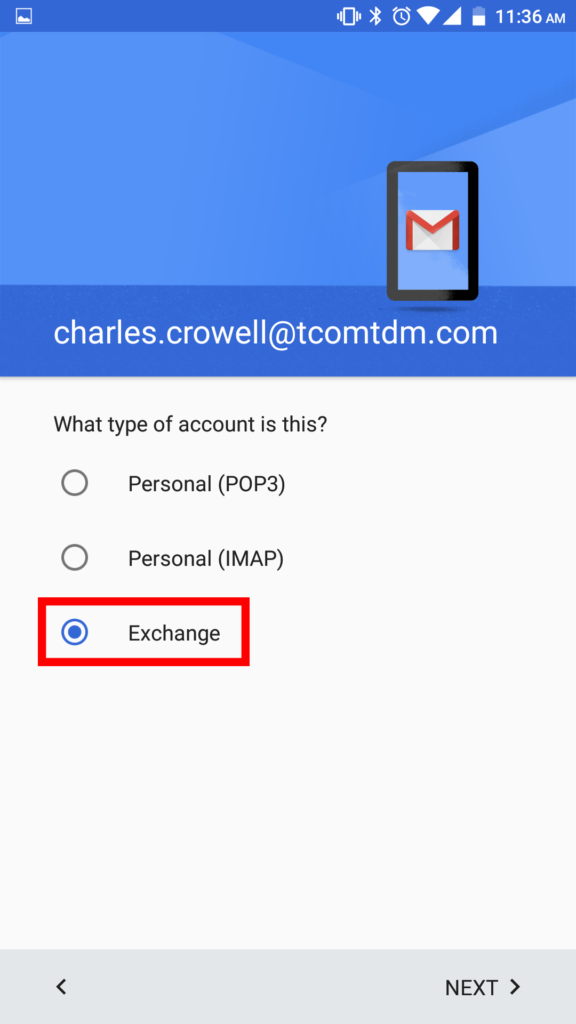
4. In accounts select Exchange.
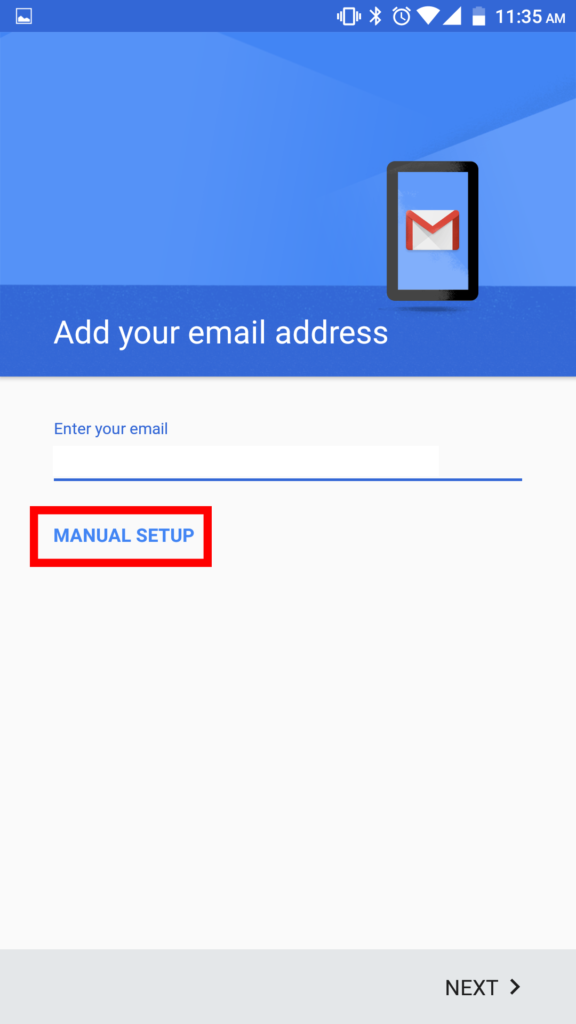
5. Next select Manual Setup.
6. Then select Exchange.
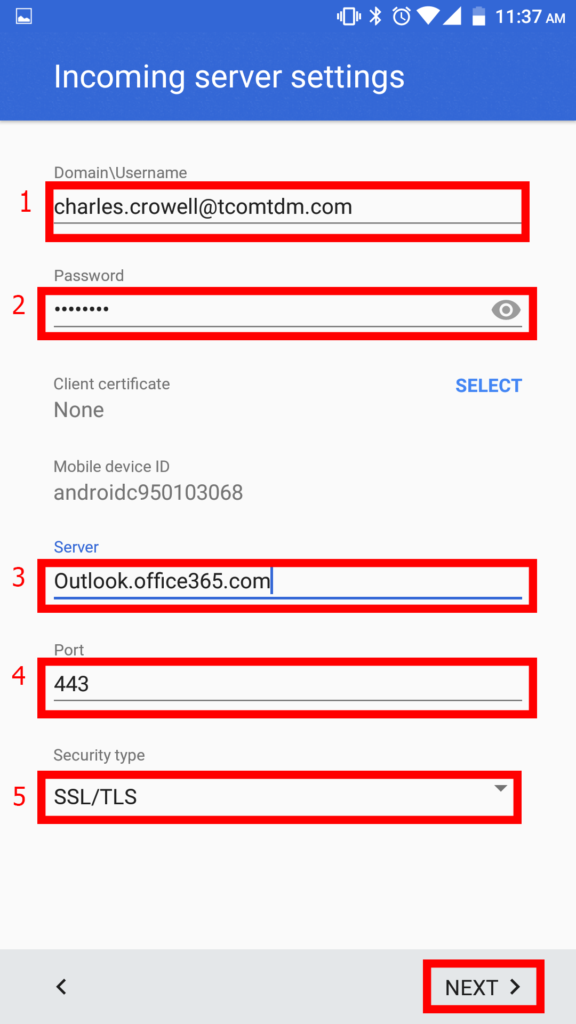
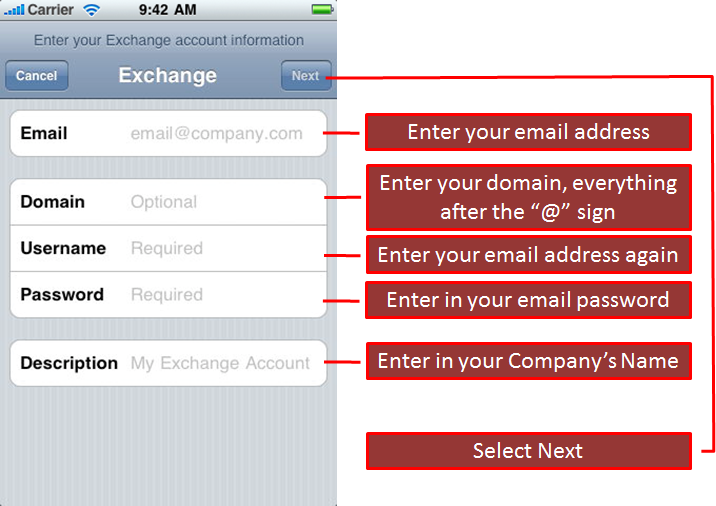
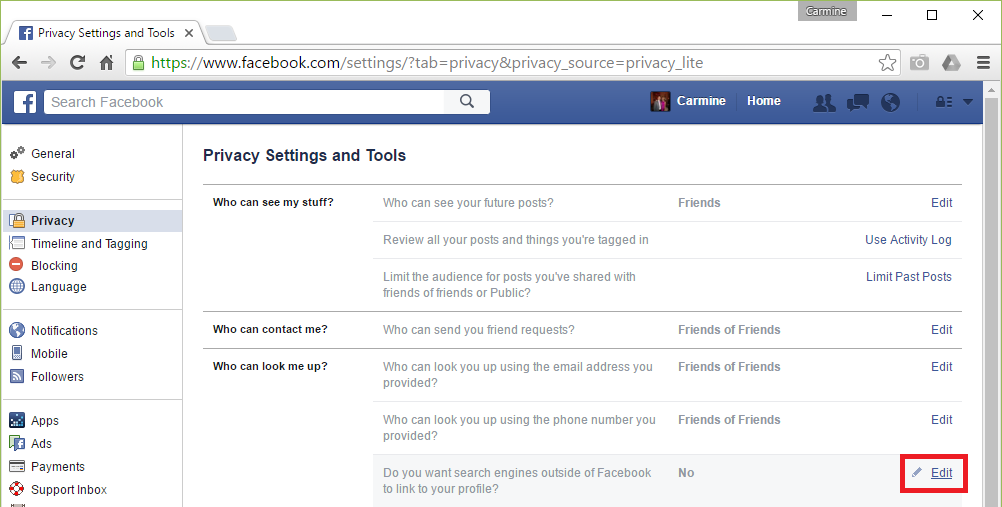
7. Now fill in the following ordered as on the screen:
1. Your email address
2. Your password
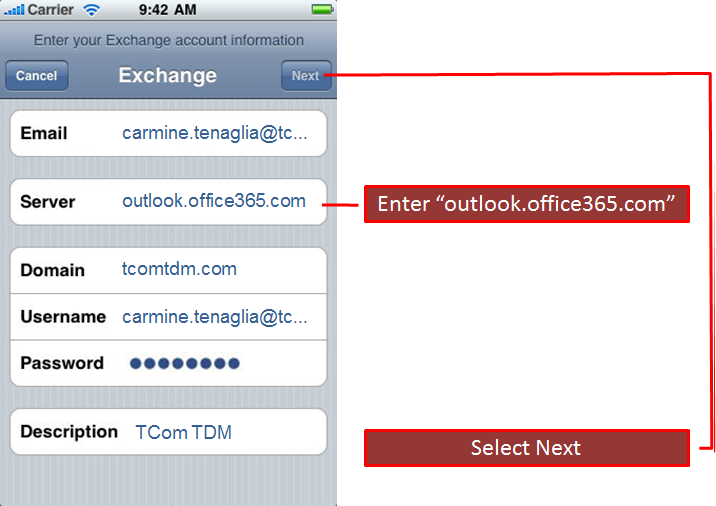
3. Under server, type in Outlook.office365.com
4. Leave Port as 443 (Change it if it is not)
5. Leave Security as SSL/TLS (Change it if it is not)
After you have filled everything in, hit “NEXT“.
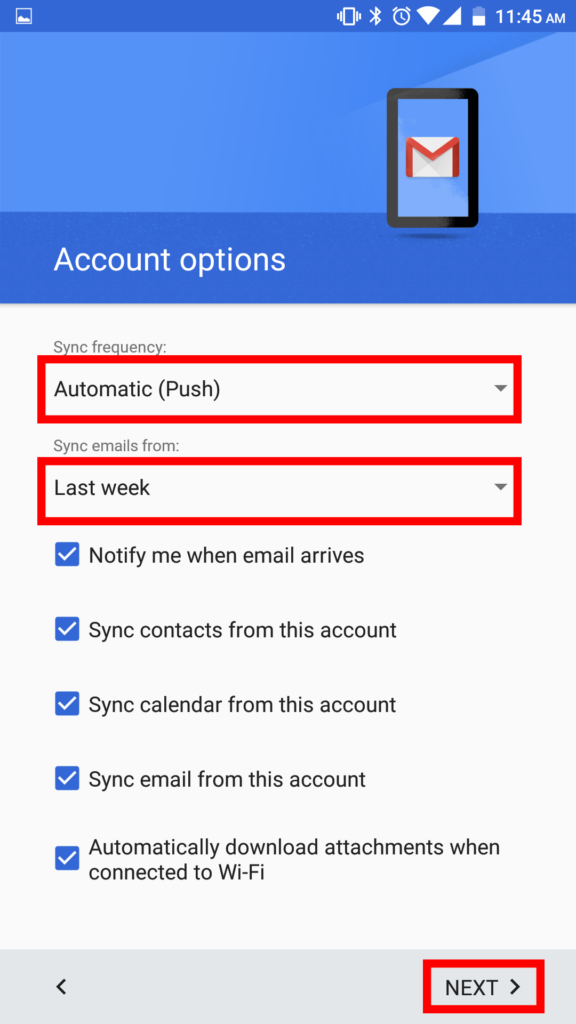
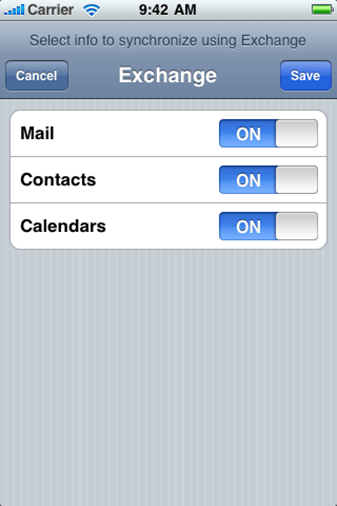
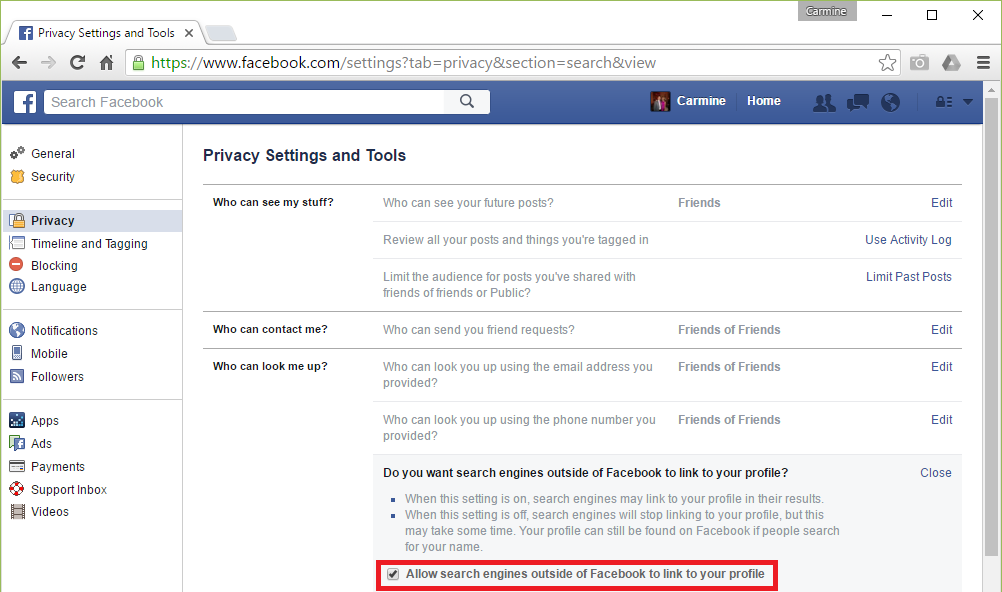
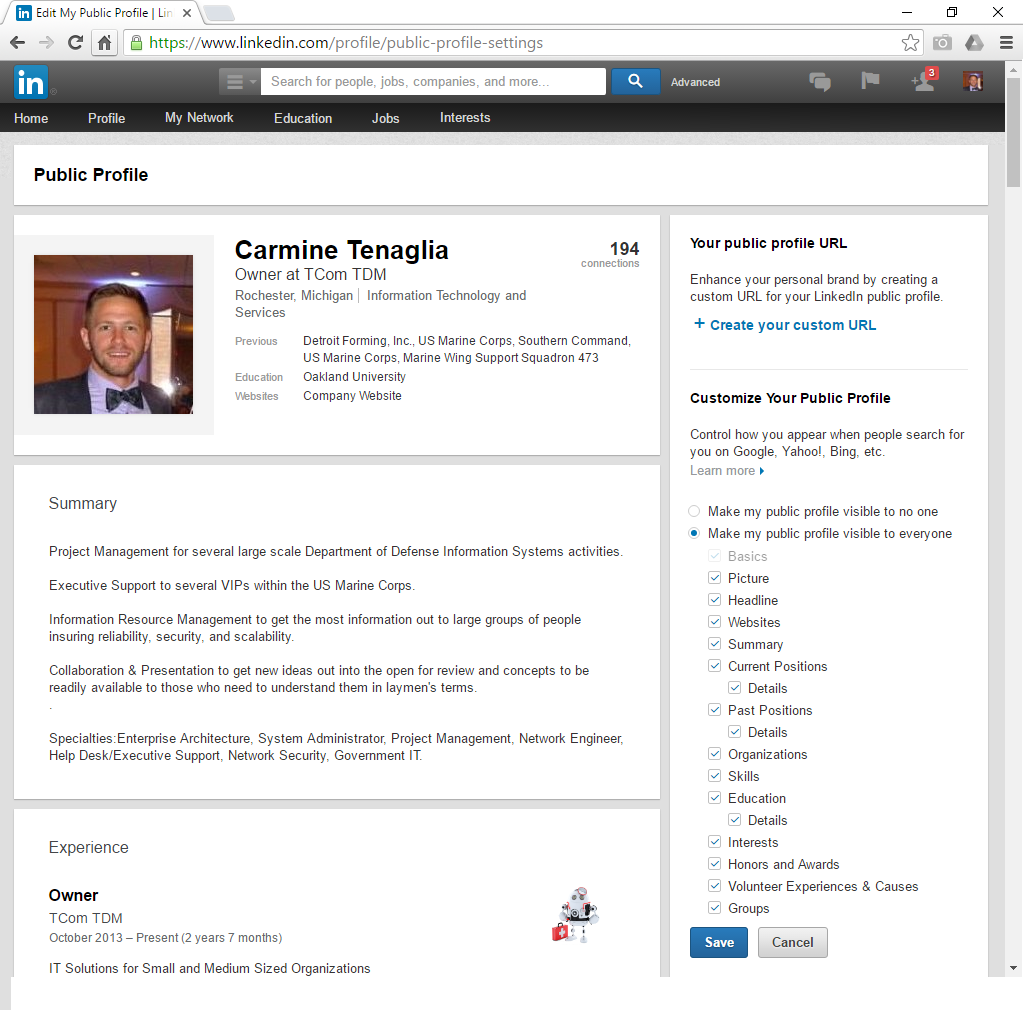
8. The first box on this screen should be set to/left as Automatic (Push). It is recommended that you “Sync” Two Weeks of emails to conserve data. Make sure all boxes on the screen are checked, unless you are instructed otherwise.
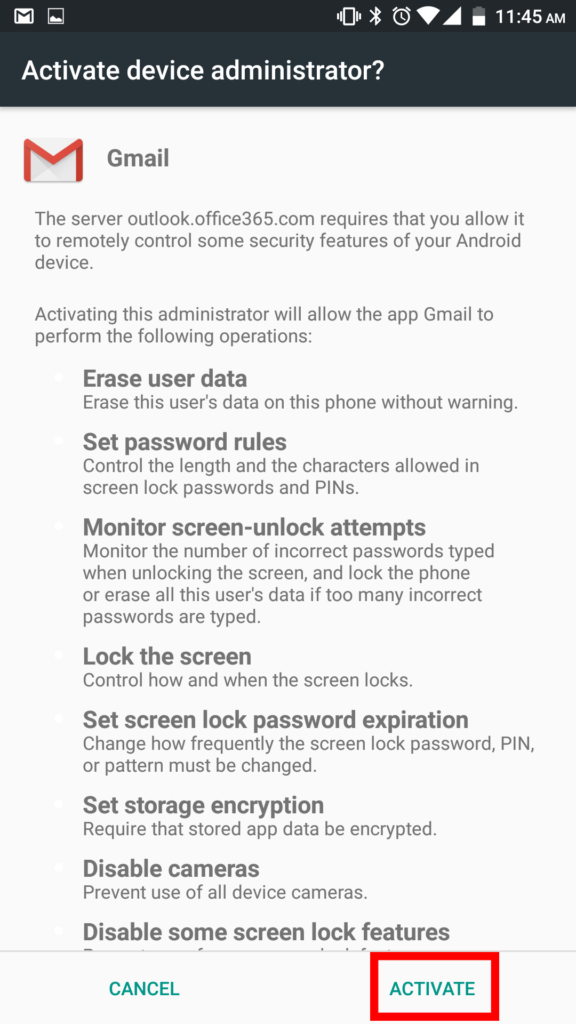
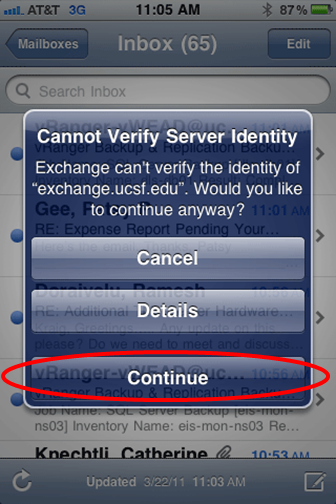
The next step may not apply to you.
9. In the case that the following shows up on your screen after completion, simply hit activate in the bottom right.
Your account should now be set up.

![P4P56EA-ABU_2_1750x1285[1]](https://www.tcomtdm.com/wp-content/uploads/2016/04/P4P56EA-ABU_2_1750x12851-848x477.jpg)
![black-nexus-5-back-on-play-store[1]](https://www.tcomtdm.com/wp-content/uploads/2014/05/black-nexus-5-back-on-play-store1-800x477.png)
![en-US-Office-Mod-E-Business-Is-Better-Office16-356-desktop[1]](https://www.tcomtdm.com/wp-content/uploads/2014/05/en-US-Office-Mod-E-Business-Is-Better-Office16-356-desktop1.png)
